From open banking APIs to security APIs, these solutions are driving a modern web-based communication, enabling them to communicate with each other. That’s why API security is becoming a growing concern.
The issue is real.
More than 41% of companies have suffered from API security incidents in the past year. This led to a 286% increase in API-centered attacks.
Companies are investing millions in API security. More than 91% of developers believe that API security should be a priority.
If you are planning to integrate an API in your solution or want to learn how you can secure your API, this blog is for you.
API: What is API Security?
API or Application Programming Interfaces are a set of instructions that allow apps to communicate with each other and conduct the transfer of data. As such, APIs are a fundamental part of microservices architecture, i.e. majority of modern software.
Now that you know what an API is, let’s see what exactly “API security” is:
The term API Security refers to the process of securing APIs against cyberattacks. Well, an API is the bridge that allows two software programs to communicate with each other. And exchanging crucial information, they are the point hackers attack first.
Though API security has a big role to play in modern software security, it also has its differences. So, before we discuss API security’s importance, let’s look at general app security and API security.
App Security vs. API Security: The Difference
| General App Security | API Security |
| Focuses on protecting the overall application from a wide range of threats | Focuses on securing the APIs that allow different software applications to communicate with each other |
| Includes implementing secure coding practices, encryption of sensitive data, authentication and access control mechanisms, and regular security audits and testing | Includes implementing access controls to limit who can access the API, using authentication and authorization mechanisms to ensure that only authorized users can use the API, implementing rate limiting to prevent overuse of the API, and encrypting data that is transmitted over the API |
| Protects against unauthorized access, data breaches, and malicious attacks | Specifically focuses on the unique risks posed by API usage |
| Important for protecting software systems from various security threats | Necessary for securing the interactions between different software applications |
| This applies to the overall application and its components | This applies specifically to the APIs and their usage |
| Helps ensure the confidentiality, integrity, and availability of the application | Helps ensure the confidentiality, integrity, and availability of the APIs and the data transmitted over them |
With that out of the way, let’s look at why API security is important.
Why is API Security Important?
Why is API security important?
Well, as we discussed, APIs are responsible for transferring important data. For instance, the Open Banking API allows fintech apps like eWallet to access a person’s bank data.
So, in case anyone manages to hack, expose, or compromise the API, it can mean a leak of personal data, financial data, and any other data of a sensitive nature. This is something that neither a business nor a user wants. And it can end up in a loss of billions, as we see every year.
Therefore, securing the API is of immense importance.
With software and app development growing in popularity, the use of API is also becoming very common. In addition to this, the number of cyber attacks is also increasing.
For that reason, securing APIs is more important than ever.
Speaking of which, let’s look at two types of API architectural styles and what the differences are between them.
REST API Security vs. SOAP Security
People often ask, What are the types of API security? And the answer to that is 2.
Well, these are SOAP and REST.
SOAP API refers to a well-structured message protocol that allows multiple low-level protocols.
On the other hand, REST API is a simpler one that uses HTTP/S in the form of the transport protocol. As such, this one uses JSON format for the purpose of transferring data.
| SOAP API security | REST API security |
| Offers protocol extension | There are no built-in security capacities |
| Based on W3C and OASIS, standards including SAML tokens, XML encryption, and XML signatures | REST API security must be integrated with data transmission, deployment, and interaction. |
| Built-in Error Handling via WS reliable messaging support. | No Built-In Error Handling. |
| Supporting Web Services Specifications. Allows extensions like WS-Security. | Deployed with an API gateway for better security. |
API Security Management
A big part of API security is API Security Management. In order to do this and secure the API, the majority of the platforms allow three major types of API security schemes.
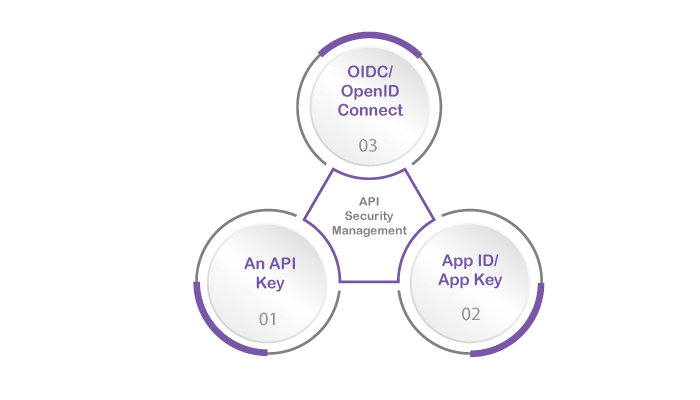
These are, as mentioned below:
- API Key – This security scheme uses a single token string. For those who aren’t familiar with the term, it is hardware that enables unique authentication information.
- App ID/App Key – This is a two-token string method that is often seen in the form of a username and password-based authentication.
- OIDC / OpenID Connect – This method creates an identity layer based on the OAuth Framework. It is used to identify users via their profile information and the authentication server.
API Endpoints
One can’t finish the API security discussion without talking about API endpoints.
These are the points of contact and communication between two APIs. In more technical terms, they are URLS and digital locations on which APIs send and receive data.
API Endpoints are highly important as they are the exact location of data exchange. If this doesn’t function properly, the API will stop working.
Well, you might be wondering why the security of web API or mobile app API is important at all. Let’s look at some of the top examples of API security breaches in the next section.
API Security Breaches Examples
Do businesses often wonder whether investing in API security is really worth it? Well, it is as important as business app development.
There are various examples of large companies losing billions and tons of sensitive data due to their API security breach.
So, let’s look at some of the most important examples.
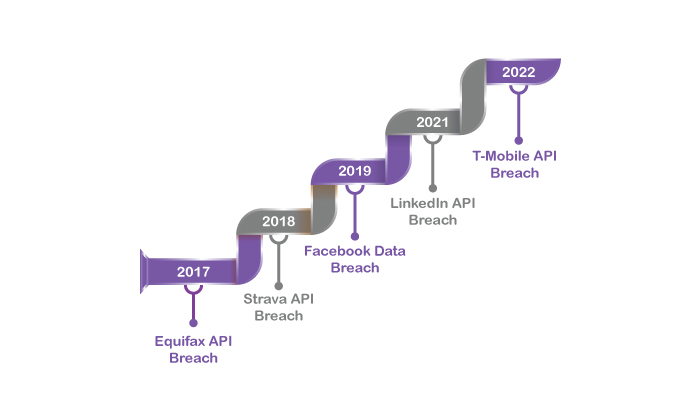
2017 – Equifax API Breach
Some 6 years ago, Equifax, a credit reporting agency, saw a huge data breach over its API. Hackers gained access to the sensitive data of over 143 million people.
2018 – Strava API Breach
Strava is a popular fitness mobile app. Well, as it turns out, it was ( is ) used by some US military personnel to track their activity.
Thus, it had some sensitive information from military bases across the globe. But, (you guessed it) the platform API breach led to huge losses.
2019 – Facebook Data Breach
Facebook is the most popular social media app right now. The platform contains the data of billions of people, including phone numbers, names, and personal messages.
But all of it was lost to a hacker back in 2019. The leak targeted two datasets from third-party Facebook apps.
2021 – LinkedIn API Breach
Well, well, who doesn’t know LinkedIn, the popular job search platform? As it turns out, the public API platform used without any authentication was breached in 2021.
The leak was so huge that the platform lost the data of 92% of its users. In other terms, this means 700 million users.
2022 – T-Mobile API Breach
T-Mobile is one of the largest phone service providers in the USA. Despite this, it faced a data breach with one of its APIs just back in 2022. Well, it resulted in the leak of 37 million users’ personal information.
With that out of the way, let’s look at some of the most common threats to API security.
API Security Threats
There are various types of threats to API security. So, before we discuss API security best practices and other things along the way, let’s look at some of the most common threats to API security.
Here are some of the most common API security breaches, as per the Open Web Application Security Project (OWASP):
| API Security Risk | Description |
| Broken Object-Level Authorization | APIs that don’t enforce proper authorization checks on individual objects can allow attackers to access sensitive data or perform unauthorized actions. |
| Broken User Authentication | An Application Programming Interface that has weak or broken authentication mechanisms can allow attackers to impersonate legitimate users, steal credentials, or perform unauthorized actions. |
| Excessive Data Exposure | If too much data is exposed, it can put sensitive information at risk of exposure or theft. |
| Lack of Resources and Rate Limiting | APIs that don’t implement proper resource management or rate limiting can be vulnerable to denial of service attacks or excessive usage. |
| Broken Function-Level Authorization | When APIs don’t enforce proper authorization checks on individual functions, it can allow attackers to perform unauthorized actions. |
| Mass Assignment | APIs that allow mass assignment of input parameters can be vulnerable to injection attacks or unauthorized access. |
| Security Misconfiguration | Again, an API misconfigured can be vulnerable to a wide range of security risks, including data breaches, injection attacks, or denial of service attacks. |
| Injection | APIs that don’t properly validate user input can be vulnerable to injection attacks, such as SQL injection or cross-site scripting (XSS). |
| Improper Asset Management | APIs that don’t properly manage assets, such as keys or tokens, can be vulnerable to theft or misuse. |
| Insufficient Logging and Monitoring | Here, APIs that don’t log or monitor activity can be vulnerable to attacks or breaches that go unnoticed. To mitigate this risk, |
How To Secure an API? API Security Best Practices
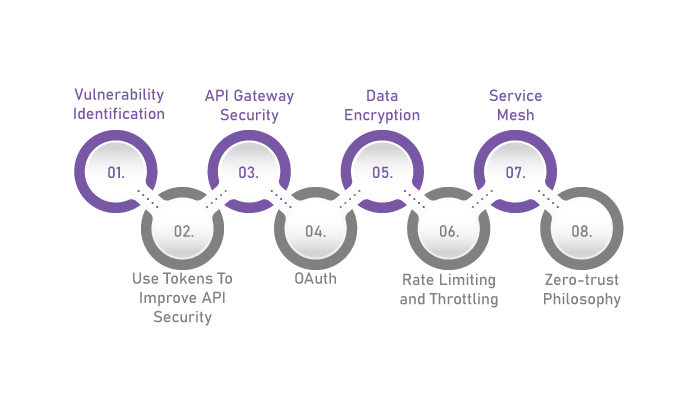
So, how do you secure an API against the security threats we discussed above? Well, there are various API security best practices. We shall be discussing a number of those here. So let’s get right into it:
1. Vulnerability Identification
It goes without saying that if you want to secure an API, you first have to identify the potential insecurities
Now, this is easier said than done. And it becomes even harder if the solution is dealing with a large number of APIs.
Furthermore, one has to consider the entire API development lifecycle. As such, all steps from planning through development, testing, staging, and production should be considered.
This is the first thing to consider.
Moving on, let’s look at the next process.
2. Use Tokens To Improve API Security
Once you are done with identifying, it’s time to improve the security system via a technology called a token.
API security tokens work something like this: the token is used to communicate, and they are required to authenticate before passing the information.
These tokens allow controlled access to resources. The reason is that any interacting software that doesn’t have a proper token will be rejected. This is how your tokens improve overall security, thus making it one of the API security best practices.
3. API Gateway Security
Well, we have heard many times the term “API gateway”.
But what is it exactly?
An API Gateway security stands as a gate between the client and the backend services. Thus, it serves as a reverse proxy since it allows traffic to pass and authenticate the same as per predetermined standards.
An API Gateway, when used with Static Residential Proxies, acts as a centralized access point for managing API calls while masking the source IP addresses with legitimate residential IPs.
In this way, the API gateway improves the security of the platform significantly.
4. OAuth
Let us introduce you to one of the most important things in the API security scenario, OAuth. As such, OAuth is a powerful tool for controlling API access.
It is a token-based authentication framework. This enables third parties to access important information without user credentials disclosure.
It allows controlled access through authentication and authorization. And for that reason, it’s quite popular among API developers.
5. Data Encryption
Here’s one of the oldest tricks in the book to secure data.
Well, data is sensitive, and one of the oldest ways to secure it is encryption. For those who don’t know, encrypting data makes it unreadable unless you have the code used to encrypt it.
API deals with a lot of data, including (and especially) personally identifiable information (PII). To ensure this data is safe, API security standards require companies to encrypt
So even if someone can get access to the data, they won’t have the code to make it readable.
6. Rate Limiting and Throttling
As we discussed previously, one of the most common types of cyberattacks against APIs is denial of service (DoS) attacks.
To protect the API against this, app and web developers often limit the frequency of API calls. It works well to protect the solution during high traffic, thus driving performance and high-end security.
Moreover, it also helps create a balance between availability and access via user connection regulation. So this is something that you must consider for securing the API.
7. Service Mesh
Service mesh is much like an API gateway. Here’s How: Service mesh technology creates a multi-layer management and control system. This happens when a service request is routing.
As such, service mesh creates the perfect flow of different parts working together, creating a streamlined process between correct authentication, access control, and other security measures.
Today, service mesh has become one of the most common technologies for APU security. Therefore, this is something that you should definitely consider.
8. Zero-Trust Philosophy
It is exactly as it sounds. Zero-trust philosophy assumes that no system is to be trusted, even if it exists within the security perimeter, until proven otherwise.
Therefore, when communicating with the API, they have to authenticate their identity, improving the overall security of the API.
Zero trust philosophy uses technologies such as OAuth 2.0, API keys, and SSL/TLS encryption, i.e., the ones we discussed above.
With all that said and done, it’s time to test the API. And here’s how we do it.
API Security Testing – Methods
Once you have implemented the API correctly according to best practices, it’s time to test the API.
As such, API security testing involves a range of techniques designed to identify vulnerabilities in APIs and ensure that they are secure from attacks.
These techniques can help organizations identify and remediate potential security risks in their APIs before they can be exploited by attackers.
| API Security Testing Techniques | Description |
| Parameter Tampering Testing | Being one of the most common, this testing method involves modifying parameters in API requests to check if the API is properly validating and sanitizing input. This can include testing for SQL injection, XSS, and other types of vulnerabilities. |
| Command Injection Testing | This is a testing technique that involves injecting malicious commands into API requests to check if the API is properly validating and sanitizing input. This can help to identify vulnerabilities that could allow attackers to execute arbitrary commands on the server hosting the API. |
| API Input Fuzzing Testing | Fuzzing Testing technique involves sending malformed or unexpected input to the API to check how it handles errors and exceptions. This can help identify vulnerabilities such as buffer overflows or denial-of-service attacks. |
| Unhandled HTTP Methods Testing | This testing technique involves sending HTTP requests using methods that the API is not designed to handle, such as TRACE or DELETE. This can help to identify vulnerabilities in the API’s handling of HTTP requests and responses. |
Top Open Source API Testing Tools

To improve API security testing, you can incorporate tools. So, let’s look at the API security testing tools below:
- Postman
- SoapUI
- Swagger
- JMeter
- Assertible
- RestAssured
- Karate
- Newman
- Insomnia
- Apache Bench
API Security Checklist
Securing an API can be difficult and confusing since there are so many steps. And to help you with just that, here’s an API Security Checklist that you may follow.
It is, as mentioned below:
- Authentication and Authorization
- Encryption
- Input Validation and Sanitization
- Rate Limiting
- Audit Logging
- Vulnerability Scanning
- Monitoring and Alerting
- API Documentation
- Penetration Testing
- Continuous Improvement
And with that, we are done with the blog.
Conclusion
API security is a rising business concern, considering its importance of API security. If you are someone new to the concept and want to integrate an API securely in your web app or mobile app, you should contact a mobile app development company.
Apart from that, we discussed all you need to know about API security. With that, we conclude the blog.
FAQ
Some best practices for API security include:
- Strong authentication and authorization mechanisms
- Encryption to protect data
- Validating and sanitizing input
- Rate limiting and throttling
- API gateway
- Monitoring and logging API activity
- Assessing the security of the API
API security testing focuses specifically on testing the security of APIs, while traditional web application testing includes testing the security of web applications as a whole. API security testing can involve both manual and automated testing techniques, such as static analysis, dynamic analysis, and penetration testing.
Some common vulnerabilities in APIs include broken authentication and access control, injection attacks, cross-site scripting (XSS), excessive data exposure, and security misconfiguration.
An API gateway is a tool that can be used to manage API traffic and apply security policies, such as authentication, authorization, and rate limiting, to incoming requests. The API gateway can also be used to log and monitor API activity, which can help to detect security incidents in real-time.
Organizations can ensure the security of third-party APIs by conducting a thorough security assessment before integrating the API into their applications. This should include reviewing the API documentation, testing the API for vulnerabilities, and verifying that the API provider has appropriate security controls in place.
API security is particularly important in the context of microservices architecture, as microservices are often interconnected through APIs, and vulnerabilities in one API can have a ripple effect throughout the entire architecture. Implementing strong API security measures can help to mitigate these risks and ensure the overall security of the microservices architecture.

Niketan Sharma, CTO, Nimble AppGenie, is a tech enthusiast with more than a decade of experience in delivering high-value solutions that allow a brand to penetrate the market easily. With a strong hold on mobile app development, he is actively working to help businesses identify the potential of digital transformation by sharing insightful statistics, guides & blogs.
Table of Contents




No Comments
Comments are closed.